All incidents are not created equal, to coin a phrase.
It is particularly true for enterprises today more than any time in history.
In the Economist Intelligence Unit (EIU)’s 2016 executive report, crises are clearly re-categorized into 3 major scopes:
- Traditional crisis
- Cyber attack, hacking, cyber crime
- Abrupt political change/issue
What constituted a company crisis 10 years, or even 5 years, ago is no more sufficient to summarize the critical risks enterprises face today, thanks to the rampant cyber crimes and volatile geopolitical tensions across the globe.
It is hence worth a whole new look at crises from a cyber perspective.
If you are not there yet, you should start to think now.
One of the myths about cyber incidents for the executives is anything “cyber” is an IT issue.
No one is to blame for that misperception though, given the fact that most senior management, actually most people, simply lack the basic knowledge about information technology, the internet, protocols, computer, network, etc.
But “Call the IT guy” is not enough when your company is hit by a cyber crisis, nor is it the right strategy.
IT is not the only function that manages cyber incidents or crisis (if a minor incident is not managed well), rather, it should be an integral part of your crisis management system.
How many companies have the IT heads on the core team of their CMT (crisis management team)? I bet few have. But nearly every company’s CMT reserves a significant seat for Communications or PR.
Because crisis communication is something we can easily see and feel, but IT?
We don’t know what to do with all this mess. I don’t even know what it means, which is which… The boss says.
It’s too technical, too IT, totally over our head.
But hold on.
When we say it’s too technical, or too IT, we all forget everyone of us has been a node or dot in the web of Information Technology.
When we write emails, we don’t think it’s too technical — we don’t realize how technical it is per se.
When we receive a phishing email, we know only better than to click on the phishing link.
There, we are being technical with that awareness in mind — we’ve learned that from the cyber security awareness poster in the pantry room, or a training last week.
That’s the point — we must know what are the assets we are protecting, and how we can do that.
That’s what cyber crisis management should start with – define (the assets), educate (the people), prepare (the response team), achieve (the goal), and the ultimate goal of any crisis management is: business resilience.
In a Deloitte report titled “Cyber Crisis Management – Readiness, Response and Recovery”, three phases were proposed as the goal for an organization:
- Secure (key: prioritize data)
- Vigilant (key: awareness and monitoring)
- Resilient (key: mitigation through institutionalized system)
The Deloitte report highlights the life cycle of CIR (Cyber Incident Response) which illustrates the similar interrelation between Disaster Recovery (DR), Crisis Management (CM) and Business Continuity Management (BCM) in the traditional sense.
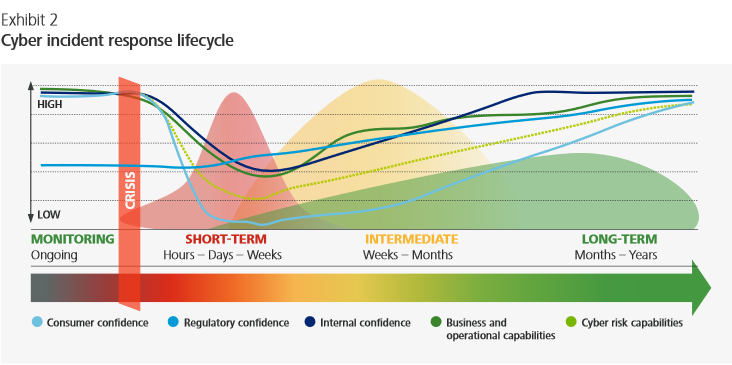
*The Deloitte report, page 5
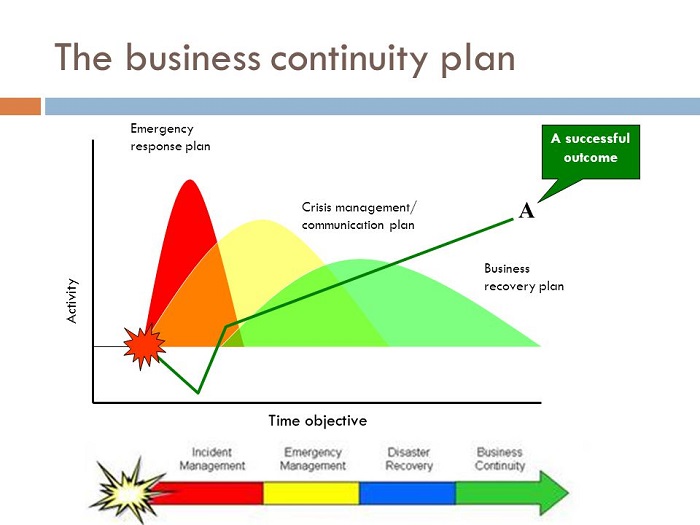
*Read the full report:
Deloitte. Cyber crisismanagement:Readiness, response, and recovery
Reference:
European Network and Information Security Agency (ENISA) recommended publication
“Strategies for incident response and cyber crisis cooperation”






